Consider a business network in which all users, devices, and applications are automatically trusted until they are found guilty. This is how traditional security models work, and businesses are vulnerable to cyberattacks and insider threats. Zero trust architecture (ZTA) is the opposite of this: all entities are not trusted by default, and every access request is checked on an ongoing basis.
With the rise in sophistication of cyberattacks and the rise in remote work, the use of perimeter-based security is no longer sufficient. Zero trust architecture makes sure that only authorized users and devices are allowed access to critical resources, minimizing risk and enhancing overall security. Companies that use ZTA are more likely to secure sensitive information, restrict insider threats, and stay in compliance with regulatory requirements.
This guide will take you on a tour of the fundamental concepts of the zero trust architecture, the main elements of this architecture, the implementation strategies, and the most frequent pitfalls. These concepts can help you start changing your security strategy to address the needs of the modern multifaceted digital world.
What Is Zero Trust Architecture?
Zero trust architecture (ZTA) is a cybersecurity framework that is developed on the basis of a single principle: never trust, always verify. Conventional security systems tend to believe that anyone within the network can be trusted; employees, devices, or applications. This is a weak assumption, particularly when an attacker is allowed to access internal systems.
Contrary to this, ZTA considers all access requests as potentially risky, irrespective of their source. This implies that all users, devices, and applications have to be authenticated, authorized, and constantly verified prior to gaining access to sensitive information or vital systems.
This is especially relevant in the current day, where the contemporary workplace is becoming more decentralized. Workers can use corporate networks at home, companies have become overly dependent on cloud services and cyber threats on the cloud keep becoming more sophisticated.
Zero trust architecture allows organizations to abandon the idea of using a network perimeter as the only protection mechanism and instead protect every interaction through continuous authentication, rigorous access control, and real-time monitoring. The model aids in averting breaches, minimizing insider threats, as well as safeguarding vital assets in a very dynamic setting.
The Main Elements of Zero Trust Architecture
Zero trust architecture is not a product or tool. Rather, it is a framework constructed of several security practices in collaboration. All elements are important to the implementation of the principle that only authorized users and devices may access sensitive resources:
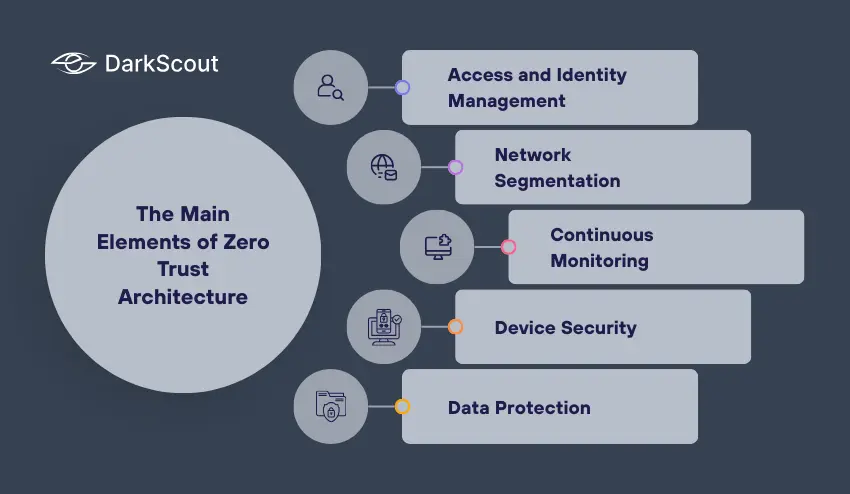
1. Access and Identity Management (IAM)
IAM is the backbone of ZTA. It makes sure that the resources required by the users are only accessed by verified users. Role-based access controls and least-privilege policies allow organizations to grant access to sensitive data to the individuals who actually require it. This reduces the harm that can be caused by hacked accounts.
2. Network Segmentation
Network segmentation separates the entire network into small and isolated areas. This helps to stop any lateral movement of attackers once they are on the network, once they have access to a segment. To illustrate, in the case of a breach in a low-risk area, high-value systems are not compromised. The segmentation plays a key role in reducing the effects of attacks.
3. Continuous Monitoring
ZTA needs real-time user, device, and application monitoring. Machine learning and analytics can detect suspicious behavior, e.g., a user accessing systems at unusual times or in unusual locations. Constant surveillance allows organizations to recognize and respond to threats before they run out of control.
4. Device Security
The devices that are connected to the network are usually a weak point. Zero trust means that all endpoints are security-compliant before access is granted. This includes validation of new software, antivirus status, encryption and compliance with company policies. Devices that are compromised or non-compliant are refused entry.
5. Data Protection
It is also critical to protect the data at rest and in transit. ZTA encrypts the data and applies access controls to ensure that sensitive data is not accessed or modified without the appropriate authorizations. This helps to mitigate the possibility of information leaks and complies with the regulations, such as GDPR or HIPAA.
You May Also Like: Types of Firewall: A Complete Guide for Beginners
How Zero Trust Architecture Operates
Zero Trust architecture is a proactive, dynamic security model based on those components. Every access request is verified, every interaction is monitored, every asset is protected, whether it’s on-prem or in the cloud.
This means in practice that:
- Remote employees can only access the systems they are authorized to access.
- A compromised device cannot continually roam freely across the network.
- Data remains encrypted and secure even if some security layers have been bypassed by a potential threat.
Visual Suggestion: A diagram comparing traditional perimeter-based security (trust inside and block outside) versus zero trust architecture (verify every access request, continuously monitor, enforce least privilege).
Principles of Zero Trust Architecture
Zero trust architecture is constructed based on a set of principles that govern how organizations think of security. These values allow trust to be never presumed and all access requests should be considered. The principles are vital in the implementation of ZTA.
1. Verify Every User and Device
No user or device is automatically trusted, inside or outside the network, in a zero trust model. All attempts to log in and all connections to a device should be authenticated and authorized. This includes multi-factor authentication (MFA), complex passwords, device health scans and ongoing verification.
2. Use the Principle of Least Privilege.
Only the resources required to complete their respective tasks should be made available to the user and the devices. Restrictions minimize the damage that a compromised account or insider threat may inflict on an organization. This principle will help make sure that even in cases of stolen credentials, attackers will not be able to access sensitive systems at will.
3. Micro-Segmentation
Zero trust architecture is based on micro-segmentation of the network, which separates the network into small and closed areas. All the segments are isolated to ensure that attackers cannot move laterally in case they have access to one segment.
Micro-segmentation can also enable the use of more specific access control policies according to user roles and the sensitivity of the resource.
4. Ongoing Observation and Analytics.
ZTA constantly tracks user activity, hardware health and network traffic. It can identify anomalies, unusual patterns, or even potential threats in real time using analytics and machine learning. Constant monitoring enables organizations to react in time, and the outcomes of harm are reduced.
5. Assume Breach
One of the fundamental tenets of zero trust is that breaches will and can occur. This mentality is what motivates organizations to develop security systems that have contained attacks, less damage, and rapid recovery. Rather than use perimeter defenses, each system layer is hardened against intrusion.
6. Data Protection and Encryption.
Zero trust gives a lot of importance to data protection. This involves encryption of data at rest and in transit, strict access controls and audit logs. Data is secure even in the event that attackers circumvent other security measures.
Why Zero Trust Architecture Is Crucial
Zero trust architecture is now mandatory to most modern organizations, not optional. The old-fashioned trust but verify methodology has loopholes that can be used by hackers, particularly in the current world of working remotely, cloud computing, and advanced cyber attacks.
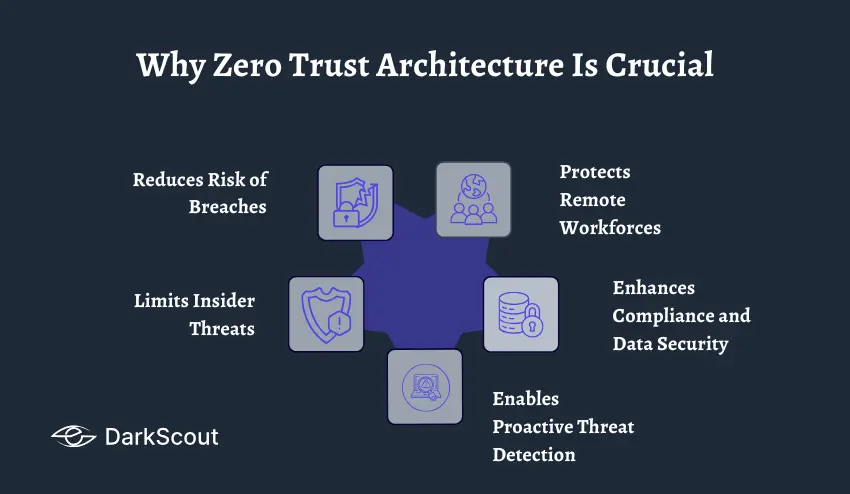
1. Reduces Risk of Breaches
Zero trust architecture severely limits the attack surface by authenticating each user, device and application prior to access. Although attackers may gain access to a single network segment, segmentation and least-privilege policies deny them the ability to move laterally and destroy important systems.
Example: A multinational financial company deployed zero trust and claimed that internal security incidents had decreased by 40 percent in the first year.
2. Protects Remote Workforces
Remote working has increased the network perimeter beyond the physical office. Zero trust architecture also allows employees and contractors to access company resources safely anywhere, without using VPNs or perimeter-based protection.
3. Limits Insider Threats
Not all threats come from the outside. Malicious or accidental insider threats can be very damaging. ZTA works on minimizing the risk from insiders as it continuously verifying access and implementing the principles of least-priviliege.
4. Enhances Compliance and Data Security
Legal frameworks like GDPR, HIPAA, and PCI DSS require that the sensitive information be tightly controlled. Zero trust architecture can help companies to meet the requirements of compliance more effectively since it is designed to address the identity check-up, constant monitoring, and encryption of data.
5. Enables Proactive Threat Detection
Zero trust enables organizations to identify anomalies in real time through continuous monitoring and analytics, instead of responding only after a breach has taken place. This is a proactive strategy that enhances the response to incidents and minimizes the possible harm.
How to Implement Zero Trust Architecture: Step-by-Step Guide–
Shifting to a zero trust architecture from a more traditional perimeter-based architecture can be very daunting. Nonetheless, when applied systematically, it can be embraced by organizations in a progressive fashion without disrupting the operations of the business. Here’s a step-by-step guide:
1. Define Your Protect Surface
Start with the definition of your protect surface instead of protecting the entire network simultaneously. This covers the most precious resources such as customer information, intellectual property, applications, and services. With the reduced scope, you can apply zero-trust controls where they are most required.
2. Map Data Flows
Once you know what to protect the next thing is to know how traffic is moving on your network. You can plot data flows to visualize who is allowed to access what, where and in what circumstances. This kind of visibility is essential in building policies that impose least-privilege access.
3. Implement Strong Identity and Access Controls
Zero trust is everything about identity. Use multi-factor authentication (MFA), single sign-on (SSO) and role-based access controls (RBAC). These are the steps that ensure that the right people get the right resources at the right time.
4. Enforce Device Compliance
Identity of a user is not enough; the device must also be secured. Implement compliance mandates, including new software, endpoint protection, and encryption, before the user is allowed to access the system.
5. Apply Microsegmentation
Break down the network into small zones that have restrictive access policies. This limits horizontal movement and should there be a breach, the attackers cannot spread easily through systems.
6. Enable Continuous Monitoring and Analytics
Zero trust is not something that is set and forgotten. Detect anomalies using behavior analytics, real-time monitoring, and logging. Security teams can respond in real-time in case of any suspicious activity, e.g. a massive transfer of data or logging in at an unusual location.
7. Start Small and Scale Gradually
A company-wide zero trust can be a complex endeavor. Instead, start with one department or application and test the model on a pilot basis. This will help IT teams streamline policies before implementing them on an organization wide basis.
Best Practices for Zero Trust Implementation
- Establish a Strategy – Prior to deploying zero trust, outline business objectives, identify critical assets, and consider what should be prioritized.
- Deepen Identity & Access – Implement MFA, SSO, and RBAC to authenticate each user.
- Implement Least Privilege Office – Provide the least access required for the function of the role, and routinely verify roles.
- Secure Devices – Implement compliance checks, endpoint protection, and encryption.
- Observe & Automate – Monitor activity in real-time and be aware of abnormal patterns, and allow automated responses.
- Train Employees – Enable awareness programs to offset human error and reduce insider threats.
- Always Evolve – Update policies and tools
Conclusion
With the increasing sophistication of cyber threats and the disappearance of the perimeter in the context of cloud and remote work, the traditional security models are ineffective. Zero trust architecture can help solve this issue by authenticating each user, device and request prior to authorization.
With a focus on identity, access control, monitoring, and segmentation, organizations provide a stronger defense against threats, gain visibility into their security posture, and adhere to compliance requirements. While it is not an overnight solution, zero trust is a scalable solution that allows organizations to adapt security to evolving risk. In our rapidly digital world, it is no longer an option to protect sensitive data and functions.



