Doxing is when someone shares your private information online without your permission. This can include your home address, phone number, email, or workplace. The goal is usually to scare, embarrass, or hurt you.
Individuals seek doxing information due to their desire to find out what it entails, how it occurs, how to avoid it or what they should do in case they are victims. Doxing is not only a problem of well-known people, and the outcomes may include online harassment and even real-life threats.
This guide defines doxing in easy-to-understand language, provides real-life examples, assists you in recognizing the warning signs at the very beginning, help you improve cyber security, and describes the steps you can take to stay safe or respond in case your personal information has been leaked.
What Is Doxing?

Doxing refers to obtaining and distributing personal or identifying information of a person on the internet, without their consent, with the aim of intimidating, harassing or harming them. It is not the discussion but exposure.
Practically, doxing transforms personal information into a weapon. The information that is being distributed might already be present on the internet, but doxing occurs when the information is actively collected, bundled, and presented in a manner that endangers the target. This usually results in harassment, threats or unwanted attention on the internet and in real life.
Doxing is not just another online research or journalism. The key difference is intent. In situations where personal information is disseminated to facilitate harassment, retaliation, or intimidation, it borders into doxing, although the information may have been publicly available.
What Information Is Typically Exposed in Doxing
Doxing can involve a single detail or a full profile. Commonly exposed information includes:
- Home address or location details
- Personal phone numbers
- Private email addresses
- Workplace or school information
- Family member names or profiles
- Links to personal social media accounts
When this information is publicized, it will allow strangers to call, intimidate or stalk the targeted individual. Limited exposure like a phone number or a city, can spiral out of control once other people are involved.
Examples of Doxing (Real-World Scenarios)
Doxing may occur in numerous situations in everyday life on the internet. The target in most instances does not anticipate a conflict or communication to turn into personal exposure. These illustrations demonstrate that doxing is a widespread phenomenon and it can happen to virtually anyone.
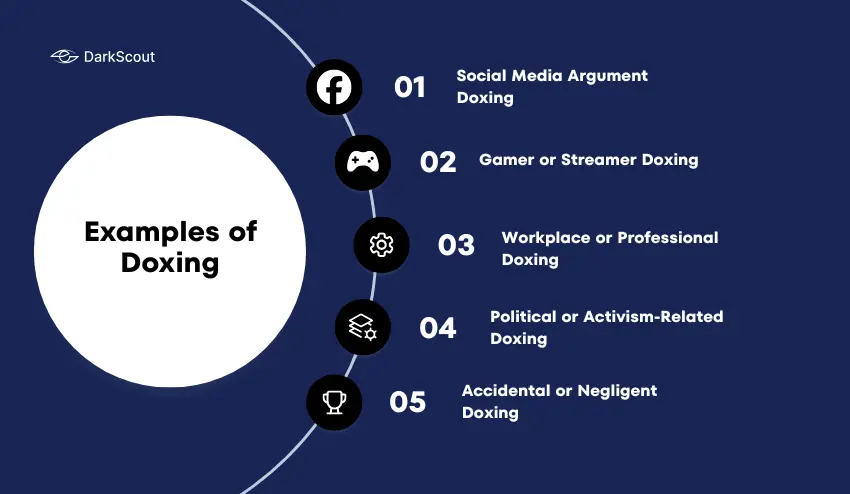
1. Social Media Argument Doxing
An online argument is one of the most widespread starting point for doxing. An argument on a platform such as X, Instagram, Reddit, or Facebook can cause one to look into the profile history of another person. Name, location, or work place can be disclosed in old posts, tagged photos or shared links.
This information is then distributed publicly once discovered, usually with accompanying screenshots, to promote harassment or humiliation. What might start as a commentary exchange can soon develop into mass targeting.
2. Gamer or Streamer Doxing
Doxing is often directed at gamers and live streamers. Attackers can use usernames, voice chat, or history of account use during streams or during multiplayer games, to determine who is on the other side of the screen.
In other situations, chat rooms or forums are used to share personal information which is used to organize harassment. The actual risk is more in this case, as live content may reveal habits, time zones or locations without any intention.
3. Workplace or Professional Doxing
In professional doxing, emphasis is made on employment. An attacker can post the name of an employer, work email, or LinkedIn profile of a person in order to coerce his or her workplace with complaints or threats.
This type of doxing is usually employed to tarnish a reputation or a livelihood. False allegations may also lead to stress, investigations or even loss of employment to the targeted individual.
4. Political or Activism-Related Doxing
Individuals in the political discourse or activism are commonly attacked due to their views. Doxing in such instances is a silencing strategy, which reveals personal details, as a way of intimidating or discouraging the masses to take part.
Such doxing is often organized, whereby groups increase the information that has been exposed to various platforms.
5. Accidental or Negligent Doxing
Not every doxing is planned and intentional. Accidental doxing is a situation when a person shares personal information without knowing it, e.g., posts a picture with addresses or documents visible, or personal information.
Though it might not be a bad intention, the outcome can be very detrimental when the information is utilized by other people to bully or attack the individual.
Is Doxing Illegal?
Doxing is either illegal or not, depending on the mode of action, the information shared, and the harm that it may cause. No universal law exists that defines all doxing as a crime; there are numerous doxing cases that are covered by the current laws concerning harassment, stalking, threats, or breaches of privacy and data.
It is all about purpose and influence. Providing personal data to promote harassment, intimidation, or physical violence is much more likely to be unlawful than merely mentioning public facts in a dispassionate manner. In a case where information is technically open, the utilization of such to threaten a person may be taken to an illegal level.
Doxing can be unlawful in cases where threats, repeated harassment, impersonation, and incitement are experienced. In such instances, the government tends to target the behavior that comes about and not the word doxing.
Doxing Laws by Region (High-Level Overview)
Doxing is a highly diverse concept in the laws of different countries, with most countries using related legislation to combat it instead of a specific crime.
- United States: Doxing can be in violation of the law concerning stalking, cyber harassment, identity theft, or credible threats. Certain states have certain cyberstalking laws that are directly applicable to the doxing behavior.
- United Kingdom: Doxing may be considered as a harassment statute, malicious communications statute or data protection statute, particularly when personal information is used to distress.
- European Union: The General Data Protection Regulation (GDPR) can be applied when the personal data is processed or transferred without any valid ground, particularly when it is harmful.
- Other jurisdictions: The privacy, defamation, and cybercrime laws are combined to address the cases associated with doxing in most countries.
Due to the fact that laws are not universal but case-specific, doxed persons tend to document evidence and seek legal advice rather than assume that something is illegal or legal.
Why People Get Doxed
Individuals are doxed to pressure, frighten or punish them publicly. Doxing is mostly carried out emotionally and not with proper planning. The triggers are anger, revenge, and ideological conflict.
Conflict situations are easy to develop on online spaces. One post, comment or opinion can be the topic of attention of people who want to dig personal information. After locating private information, sharing it is one of the methods to silence or intimidate the target.
Doxing is also a control tactic. Exposing personal information, attackers also strive to transfer a conflict to the real world, where the effects are more severe and intimidating.
Who Is Most at Risk of Doxing
Although anyone can become a victim, some groups are at more risk due to visibility or perceived influence:
- Activists and advocates: these are activists and advocates who talk about social issues.
- Whistleblowers and journalists who write on controversial issues.
- Gamers, creators, and streamers with a following.
- Owners of small businesses are a brand in the online world.
- Every day, users engage in heated online debates.
Living in danger does not imply that one has done something bad. Doxing is not concerned with the actions of the targeted person but with the abuse of information.
How Doxing Happens (Common Methods)
There are various ways of exposing personal information online. Hackers tend to mix up information that is publicly available, neglected online footprints, and reckless sharing behaviors. The knowledge of these techniques allows recognizing the weaknesses and being safe.
Key ways people’s private info gets exposed include:
- Open Source Intelligence (OSINT): Collection of data that has already been posted online, including social media posts, forums, and archived material.
- Data Broker Exploitation: Gaining or acquiring databases containing personal information.
- Social Media Oversharing: It is the accidental sharing of identifying information on posts, photos, or check-ins.
- Breached Accounts: This involves linking identities across sites with emails or passwords that have been leaked on other sites.
- Username Reuse: Following a single username through the various sites to learn more about an individual.
How Small Data Leaks Add Up
Even minor details can be harmful when combined:
- Several accounts can be connected to a phone number or email.
- Locations can be disclosed through photos that have visible street names or places of work.
- Routine, hobby, or school/work can be mentioned publicly and make a full profile.
The amplification of information can happen in phases: initial exposure to information/news/story/etc. through social media/internet, and subsequent distribution by other people online. It is critical to be informed of these patterns to prevent and detect in early stages.
How to Detect If You Are Being Doxed
Early awareness of the symptoms can prevent damage before it becomes worse. Detection is aimed at monitoring suspicious online behavior and verifying the availability of personal data in public.
Early Warning Signs Online
- Messages or references on suspicious accounts with references to personal information.
- The dangers or intimidation based on the information that is known only to you or a few.
- Unplanned account investigation, such as multiple attempts to log in or connect with unknown people.
Signs Your Personal Information Is Being Shared
- Personal information (posts, screenshots, or comments).
- Anonymous posts or comments about or containing your personal details.
- Notifications by friends or followers that they see personal information on the Internet.
How to Check What Information About You Is Public
- Self-search: Search engines: Search your name, email, phone number, and usernames.
- Surveillance tools: Install notifications on the mention of your personal data.
- Data broker awareness: See whether your information is listed on data broker sites and turn it off if you can.
It is also possible to proactively ensure that you are tracking your digital footprint so that you can respond promptly and mitigate risk. Early warning enables you to lock down accounts, delete sensitive data, and report cases until they get out of control.
What to Do If You Have Been Doxed (Immediate Actions)
In case of exposure of your personal information, a prompt action will minimize the damage and safeguard your wellbeing. The following steps are concerned with digital and physical actions.
First 24 Hours After Being Exposed
- Protect your accounts: update your passwords, use multi-factor authentication, and understand account recovery.
- Document evidence: Save posts, messages, or threats on a screen to document.
- Inform close people: inform friends, relatives or coworkers who might be impacted too.
Reporting & Legal Steps
- Report to platforms: Report to social media, forums, or websites using reporting tools to take down posts and block perpetrators.
- Report to the police: Give written records when there is threat, harassment or stalking.
- Report to other parties involved: Report to your employer, school or other institutions that are involved to avoid the risk.
These steps will make sure that you take control of your accounts again, record the incident correctly and contact the relevant authorities to safeguard yourself. Early action will stop the escalation and reduce the effects of exposure.
How to Prevent Doxing
The best method of minimizing risk is protecting your personal information online. Prevention is aimed at managing the information available, account security, and digital hygiene.
Lock Down Your Online Presence
- Check privacy settings of all social media accounts.
- Restrict the post, photo, and friend lists to those who are trusted.
- Close old or unused accounts with possible personal data.
Remove Personal Data from the Internet
- Unsubscribe to websites that are data brokers and gather information about people.
- Ask search engines to remove personal information in their search results where applicable.
- Do not leave sensitive information on the internet in open posts such as addresses, phone numbers, and work information.
Strengthen Account & Identity Security
- Use passwords that are unique and strong and use a password manager to keep track of them.
- Turn on multi-factor authentication.
- Use separate emails when dealing with personal, professional, and public to minimize exposure.
These measures will always assist in controlling what you post on the internet and will complicate the task of attackers collecting information. Frequent inspection and maintenance are the major aspects of protection in the long run.
You May Also Like: 6 Best GlobalProtect Alternatives for 2026
Conclusion
Doxing is a deliberate act of exposing personal information on the internet and it may be directed at anybody. Being aware of what it is, how it occurs, and what to be aware of can make you safe and respond promptly in case your information has been leaked.
Prevention is the greatest offense. Account security, posting less information on the internet, and looking at your online profile will reduce the chances of becoming a victim. In the event that you discover that your information has been leaked, you should stay calm and act immediately, and some of the measures that can be undertaken include locking accounts, taking notes, and reporting to sites or law enforcement, which will aid in preventing further harm.
By being vigilant and monitoring realistic precautionary steps, you will be in control of your personal information and reduce the dangers of being exposed online. To be on the safe side, it could be a nice idea to check your privacy settings on a regular basis, minimize the information you leave publicly, and install a monitoring tool to detect any possible warning signs in time.