In the age of digitalization, one weakness can destroy your whole network. Cyberattacks are rapidly changing, and companies of any size are exposed to the threat of data leakage, ransomware, and system shutdown. That is why a network security scan is necessary.
A network security scan is not merely a technical test, but a proactive measure to detect vulnerabilities, track threats, and secure your systems before they are compromised by an attacker. In this guide, we will tell you what network intrusion security scans are, why they are important, how to conduct them efficiently, and the tools that can provide you with real-time protection. By the end, you will have practical steps to take to reinforce your network and keep ahead of cyber threats.
What is a Network Security Scan?
A network security scan involves a thorough examination of your network to detect vulnerabilities, misconfigurations, and possible entry points to attackers. It scans devices, servers, routers, and endpoints that are connected to identify weak points before they are attacked.
Network security scans are either automated or manual and they assist organizations to have a secure infrastructure by:
- Identifying open ports, out-of-date software, and weak passwords.
- Observing network traffic to identify anomalous traffic.
- Detecting possible insider risks or poorly configured devices
With the regular scanning, businesses can mitigate the risk of breaches, ensure compliance, and uphold operational integrity.
The importance of Network Security Scan.
Network security scans are important in securing your organization against cyberattacks. Their significance can be summarized in two points:
1. Active Threat Detection
The scanning of your network will help you to know the weaknesses before they are used by attackers. This can be unpatched software, open ports, or weak passwords.
2. Compliance and Risk Management:
Most industries have a need to perform network scans on a regular basis to comply with regulatory requirements such as GDPR, HIPAA, or PCI-DSS. Frequent scans are used to show due diligence and minimize legal or financial fines.
Periodic network security scans also offer information on the health of your network to make sure your IT infrastructure is safe, stable, and robust against attacks.
Types of Network Security Scans
Knowledge of the various network security scans is important to enable you to make the right decision on the approach to use in your organization. The key ones are:
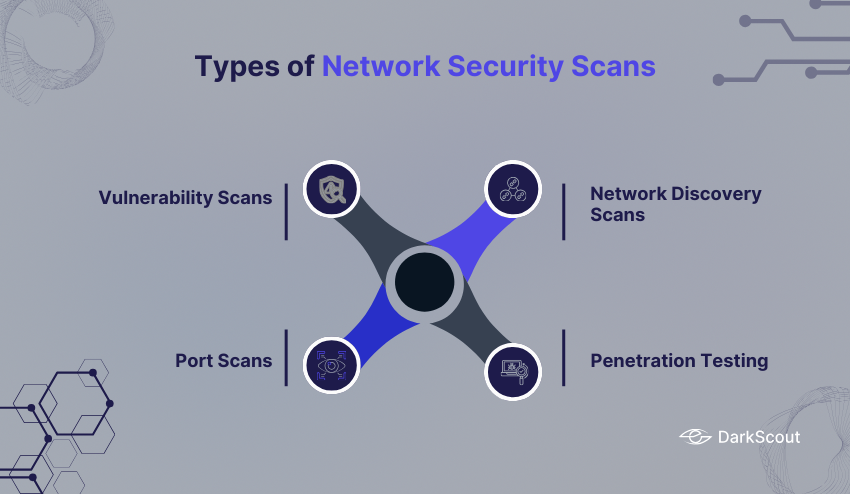
1. Vulnerability Scans:
These scans identify known weaknesses in software, hardware, and network devices. They give a list of prioritized risks to enable you to tackle the most important risks first.
2. Port Scans:
Port scans scan what TCP and UDP ports are open on your network. Open ports are possible entry points of attackers and it is therefore important to identify and secure them.
3. Network Discovery Scans
These scans provide a map of your network, listing all of the connected devices. They assist in making sure that unauthorized devices have not connected to your network.
4. Penetration Testing (Pen Test):
A more sophisticated method, pen tests attempt to mimic real-world attacks in order to determine how well your network can resist efforts to break security.
When these scanning methods are used strategically, they can provide you with a thorough picture of the vulnerabilities of your network and help you to beef up your defense.
How Network Security Scans Work
Network security scans are a methodical examination of your network in regard to vulnerabilities and weak areas. The process usually follows the following manner:
- Identify Network Assets:
The scan begins with the enumeration of all the devices, servers, and endpoints connected to the network. Knowing about all the assets helps to avoid the possibility of missing a device
- Scan Vulnerabilities:
Scanners scan open ports, outdated software, misconfigurations and other potential weaknesses. They correspond to the known databases of vulnerabilities
- Analyze Results:
The scanner generates a detailed report of the risks, their severity and the effect it can have on operations.
- Recommend Remediation:
The scan provides practical advice on how to fix vulnerabilities, close open ports, and improve security policies depending on the scan results.
Network security scans can assist businesses in detecting threats before they occur, reduce attack surfaces, and ensure their compliance with security regulations.
Benefits of Network Security Scans
The advantages of conducting regular network security scans to businesses include:
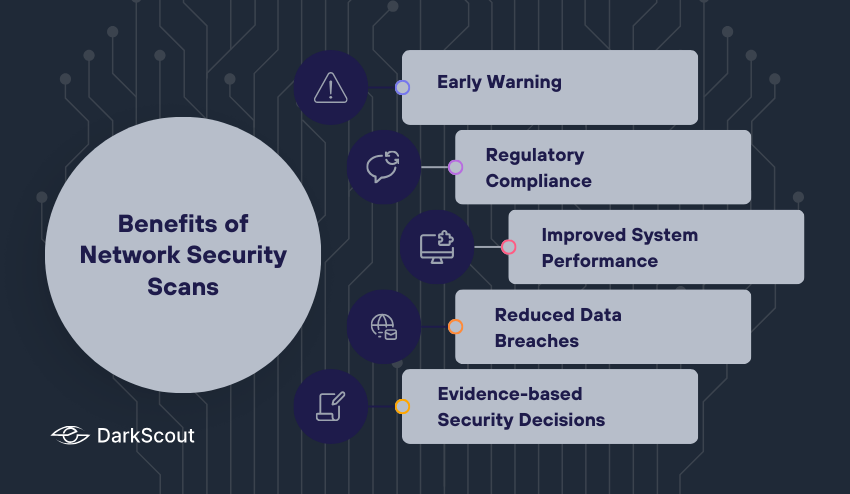
1. Early Warning
Scans identify weaknesses and suspicious traffic before the attackers can exploit them. This offensive approach will prevent potential infringements
2. Regulatory Compliance
A wide range of industries require regular security assessment. Network scans can help to adhere to such regulations as GDPR, HIPAA, or PCI-DSS.
3. Improved System Performance
Scans may assist in maintaining the network in good shape by identifying outdated software, misconfigurations, or services that are not needed.
4. Reduced Data Breaches
By detecting vulnerabilities early enough, there is less chance of someone accessing sensitive information of the company and the customer.
5. Evidence-based Security Decisions
Scans provide reports that can be utilized to prioritize security activities which is an actionable insight.
Regular network security scans are required to provide a secure, reliable and compliant IT infrastructure.
Common Network Security Scan Problems and Limitations
As much as network security scans are crucial in protecting systems, they do not come without their challenges. Being aware of these limitations can help you to use them in a productive way
- False Negatives and Positives: There are instances when scans will detect safe activity as a threat or fail to detect actual vulnerabilities. This can lead to unnecessary panic or unmitigated risks
- Resource Usage: The intensive scans can make network performance to be slow and network availability can be affected especially on large networks.
- Partial Coverage: Some network devices or obscured endpoints can not be scanned leaving potential security holes.
- Complex Interpretation: The results of the scan are normally complex to interpret. The results can be misinterpreted and result in the wrong security decisions.
- Rapidly Evolving Threats: New vulnerabilities are being formed at an alarming rate. A scan can only provide an image at a particular time and may not be in a position to detect an emerging threat.
Knowing about these concerns, the IT teams will be able to create additional measures, such as a combination of automated scans and manual checks and constant monitoring.
Best Practices for Network Security Scans
Network security scans are best performed through a purpose, regularity and frequency. To take advantage of network security scans, follow these best practices:
- Regularity: Perform the security scans at regularly set intervals; e.g. weekly, monthly, or after significant network changes. Identifying vulnerabilities early enables a quicker incident response.
- Multiple Types: Combines vulnerability scans, port scans and compliance scans to scan all avenues of a possible exploitable surface.
- Target critical systems: When scanning, look for critical systems, sensitive data repositories and internet-facing devices first.
- Stay Current: Update your scanning tools to recognize all recent vulnerabilities and exploits.
- Investigate and Respond: Make sure you do not only have a report after your scans. Look properly at what the review is telling you, prioritize the risks resulting from the review and fix them with urgency.
- Record and Track Results: A record of scanning results and actions taken should be maintained to keep track of your efficiencies in the long term and potential compliance obligations.
By adhering to the best practices for network security scans you will make the most gains from scanning and be improving the security of your overall organization.
Tools and Technologies to Network Security Scans
1. DarkScout
- Summary: A next-generation network security scanner capable of finding subdomains, detecting ports, and discovering vulnerabilities.
- Capabilities: Live tracking, in-depth reporting, and mapping of hidden services.
- Best Suited: Pen Testers and enterprise security teams who are interested in proactive monitoring of threats.
2. Nmap
- Description: This is an open source tool which is most popular as a network mapping tool and port scanning tool.
- Capabilities: Device discovery, open port scanning, OS and service identification, and has a scripting engine to automate actions.
- Best: Network reconnaissance security professionals who want to dive deep into the topic.
3. Nessus
- Description: It is a full-fledged vulnerability scanner which can detect misconfigurations and patch deficiencies.
- Features: Good reports that summarize the severity level and confirm remediation
- Best Suited To: Organizations that want to manage their risk and apply the vulnerabilities in a timely manner.
4. OpenVAS
- Description: An open-source vulnerability scanning tool, which examines most of the network services and web applications.
- Features: Routine updates to add new security threats
- Best: Small-to medium-sized organizations that need an inexpensive vulnerability assessment tool.
5. Qualys
- Description: Provides cloud security. Automated scans and checks on compliance.
- Features: continuous monitoring, scalability, and large dashboards.
- Best In: Large organizations that require real-time visibility and scalable security testing.
Conclusion
Network security scans help detect those vulnerabilities before they can be abused so that the organization has an improved cybersecurity posture and is steps ahead of all threats.
By selecting the appropriate scan, whether a port scan, vulnerability scan, or full assessment, the organization will be able to have an outcome that makes the best use of resources. The scanners using tools such as DarkScout make it much simpler to provide more details and a clear report.
Conducting regular audits of your network and addressing vulnerabilities in a timely manner, can only improve your overall network security, reduce risk, and protect sensitive data. Quite simply scanning for vulnerabilities is the best choice for keeping safe in a modern, ever-changing, threatening landscape.



