Most cyberattacks don’t start with alarms. These begin quietly and go through networks unnoticed until data is stolen, systems fail, or operations come to a standstill. It is usually too late by the time the damage is evident.
Network intrusion detection provides organizations with the possibility of identifying suspicious activity and malicious behavior in real-time. Intrusion detection systems do not respond to a breach, but instead they scan network traffic in real time to reveal threats that are missed by conventional defenses.
A network intrusion detection system (NIDS) offers the visibility required to identify known attacks, abnormal behavior and unauthorized access early. This guide will teach you the operation of network intrusion detection, the key types of IDS, and the tools and best practices that can be used to protect current networks.
What is Network Intrusion Detection?
Network intrusion detection is the work of checking a network on suspicious activity or unauthorized access. Its main aim is to recognize possible threats, malware or attacks on the fly, in order to enable organizations to react before massive damage is done.
In contrast to firewalls, which prevent some traffic, intrusion detection systems center on identifying anomalies and malicious action in network traffic.
Intrusion detection has two primary types of systems, which are IDS (Intrusion Detection System) and IPS (Intrusion Prevention System). An IDS notifies the administrators of suspicious activity, whereas an IPS proactively blocks or reduces the threat. The distinction between IDS and IPS is important to consider when designing a network intrusion detection policy.
Network intrusion detection systems have more advantages than threat alerts. They enhance visibility of the entire network, assist organizations in meeting regulatory mandates, and offer important data to analyze incidents. With the help of the IDS in your cybersecurity plan, companies will be able to secure sensitive data, minimize downtime, and improve their protection against internal and external attacks.
How Network Intrusion Detection Works
Network intrusion detection is based on observing and examining network traffic in order to identify suspicious or malicious activity. Three major detection methods are in use:
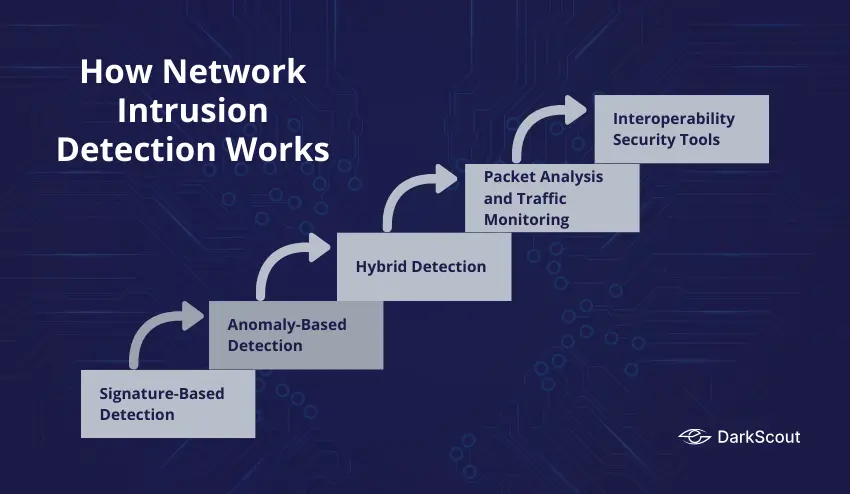
1. Signature-Based Detection
This technique matches network traffic to a list of known threat signatures. In case of a match, the system sends an alert. The signature-based detection works well in detecting a known attack but fails to detect a new or unknown threat.
2. Anomaly-Based Detection
Anomaly-based detection compares normal network behavior and indicates an anomaly with the baseline. This technique is an effective proactive network intrusion detection tool because it is able to detect zero-day attacks and abnormal patterns.
3. Hybrid Detection
Other systems integrate signature and anomaly methods, providing a middle ground solution that will be able to identify both known and new threats. Hybrid systems are more covered and less false positives.
4. Packet Analysis and Traffic Monitoring.
The intrusion detection systems scan packets that traverse the network, and compare patterns in real time. IDS can identify malicious traffic by looking at packet header, payloads, and traffic pattern, including port scanning, suspicious logins, or malware traffic.
5. Interoperability with Other Security Tools.
In today’s IDS, they are often included as part of firewalls, Security Information and Event Management (SIEM) systems, and endpoint protection platforms that allow for faster response time and greater visibility across the network creating a better security posture.
Understanding how a network intrusion detection system operates will give organizations the ability to choose the proper approach, tool, and configuration to protect their networks.
Types of Network Intrusion Detection Systems
Organizations need network intrusion detection systems (NIDS) in three primary forms, which are typically used depending on organizational requirements:
1. Network-Based IDS (NIDS)
NIDS is a network traffic monitoring tool that operates at strategic locations like routers and switches to identify suspicious network traffic. It scans the packets entering and leaving the system and notifies the administrators of possible risks.
- Advantages: Gives a general perspective of the traffic on the network; may identify attacks on more than one device.
- Disadvantages: Low visibility of encrypted traffic; sensor positioning is paramount to success.
2. Host-Based IDS (HIDS)
HIDS is deployed on individual devices or servers and scans system logs, file integrity, and local activity to identify intrusion. It is good to identify attacks not captured by network monitoring.
- Advantages: In-depth understanding of single host activity; capable of identifying insider threats.
- Disadvantages: Intensive in resources; must be installed and maintained on every host.
3. Hybrid IDS
Hybrid systems are a combination of both network-based and host-based detection systems and offer a full range of monitoring and detection abilities. They use the advantages of NIDS and HIDS.
- Advantages: Improved coverage; lower blind spots; more complex threats are detected.
- Disadvantages: It can be more costly and complicated to implement; it needs professional management.
The selection of an appropriate type of network intrusion detection system is based on the size of the organization, the complexity of the network, and the extent of threat tracking required. Proper IDS implementation will guarantee full visibility, quicker threat identification, and enhanced security of the network.
Popular Network Intrusion Detection Tools
1. DarkScout
Overview: DarkScout provides real-time full spectrum monitoring across almost all network activity; networks, endpoints, applications. Security teams visualize threat levels quickly in order to measure or track cataloged suspicious activity; allowing for proactive response. It is designed to be utilized by enterprise large scale networks as well as hybrid cloud deployments.
- Use Cases: Enterprise network security, endpoint monitoring, app protection and cloud and hybrid systems.
- Pros: Full spectrum coverage, real-time threat alerts, intuitive dashboard, easily scalable and integrates with existing security tools.
- Cons: Costly, initial implementation may require complex planning, very demanding for resource intensive deployments.
2. Snort
Overview: Snort is an open-source IDS system that has been in wide use for some time, relies on signature-based detection to recognize threats. It can log network traffic, and alert if your system is under attack, which makes it a very flexible and powerful tool for monitoring network traffic. As a widely used open-source project, Snort benefits from a sizable community presence, and often has regular updates and community support.
- Use Cases: Small to medium networks with a need for an open-source IDS solution that can be tailored to their networks.
- Pros: Free, highly configurable, well documented, strong community support.
- Cons: Configuration can be hard for novice users; signature based detection may miss new attacks.
3. Suricata
Overview: Suricata is essentially an IDS system that combines signature and anomalous detection. It is capable of quickly performing high-performance IDS as well; even while monitoring high bursts of network traffic. Suricata can provide multi-threading support allowing large volumes of network traffic to be examined at the same time, meaning Suricata analysis won’t slow down traffic on the network.
- Use Cases: Medium to large networks that depend on real-time detections and wide array of effective capabilities.
- Pros: Open-source, flexible, high-performance available, configurable.
- Cons: Configuration can be time-consuming for complex networks requiring considerable planning effort.
4. Zeek (Bro)
Overview Zeek is a behavior analysis (network behavior analysis specifically), and deep packet inspection, but not necessarily signature-based matching. It also has the potential to offer the greatest detection of advanced threats, unusual behavior and previously unknown attacks. Its optimal application is in research and businesses.
- Applications: Forensics monitoring of enterprise, behavioral analysis and threat research.
- Advantages: High-quality detection of sophisticated attacks, scalability and support to large industrial networks, analytics.
- Cons: Steep learning curve, technical acumen and talent are required.
5. Palo Alto Networks
Overview: Palo Alto Networks are a commercial IDS/IPS that generates and utilizes their own threat intelligence, and offers enterprise-level advanced capabilities to detect sophisticated threat types. It utilizes single pane of glass through integration with other security tools and enables a centralized management of security tools to enhance analytics, response and reporting efficiencies.
- Use Cases: Vendor to enterprises that require advanced security analytics, and automated analytical threat response.
- Advantages: High level of capabilities, good knowledge of the vendors, enterprise-level, simple integration.
- Cons: It is costly and is subscription-based and might need some training to get it to work.
6. Cisco Firepower
Overview: Cisco Firepower represents a hybrid of intrusion detection and prevention, and next generation firewall capabilities. Firepower depends on analytic techniques and automation to provide threat identification and response. Firepower has more ‘connectivity’ than just as simply IDS/IPS by connecting with the rest of its security tool suite.
- Use Cases: Organizations that desire to have integrated security systems that are centrally managed.
- Advantages: Organization support and advanced analytics through integration within the Cisco ecosystem.
- Cons: Costly, requires qualified personnel to install and operate.
7. Fidelis Network Security
Overview: Fidelis is a behavioral analysis, deep packet inspection software to identify the presence of advanced threats. The analytical reporting is useful to help security teams to learn the ways the attacker did it and the timelines of the incident response.
- Use Cases: Organizations with large networks and the need to detect threats and network analytics.
- Pros: Excellent security detection and reporting, it is applicable in complicated networks.
- Cons: More costly, requires skilled personnel, and is difficult to set up in large settings.
Best Practices for Network Intrusion Detection.
Installing a network intrusion detection system (NIDS) is not the end. To achieve the best outcomes, organizations must adhere to best practices that would make sure that threats are detected in a timely manner and addressed efficiently.
1. Maintain Your Detection Rules.
Intrusion detection tools are based on signatures, rules or behavior models. Unless these are updated on a regular basis, the system will fail to identify new and emerging threats. Ensure that your IDS is linked to active update feeds or that it is manually updated to identify the most recent attack patterns.
2. Combine Signature and Anomaly Detection.
Signature-based detection alone may leave new or unknown threats without any blind spots. You can reduce risks and coverage by using signature detection (known threats) and anomaly detection (suspicious or unusual patterns).
3. Monitor in Real Time
Cyberattacks are usually rapid. A real-time monitoring system is in place to make sure that suspicious activity is noted as soon as possible so that your team can intervene before significant damage is done. Keep ahead of threats using dashboards, alert and reporting capabilities.
4. Integrate with Other Security Tools.
An IDS is most effective when not a stand-alone. Its combination with firewalls, SIEM systems, and endpoint protection will result in a more robust security model that disseminates information between various levels.
5. Conduct Train Security Teams on a Regular basis.
An instrument is as efficient as the individuals operating it. Frequent training can assist your team to decipher alerts, identify false positives, and act promptly in response to real threats. The most effective IDS may not be effective without experienced personnel.
6. Periodically audit Logs and Reports.
There are logs and reports that are rich in information on network activity. Their review is useful to determine common problems, learn the patterns of attacks, and enhance system settings with time.
7. Periodic Security Audits.
Cybersecurity is not stagnant. Conducting periodic audits will make sure that your IDS is operational and that it keeps up with the dynamic threat environment. This also assists in determining loopholes in coverage before they are used by attackers.
Network Intrusion Detection Challenges
Although network intrusion detection systems (NIDS) are effective, they are not flawless. Knowledge of these limitations assists organizations in planning and in avoiding the pitfalls.
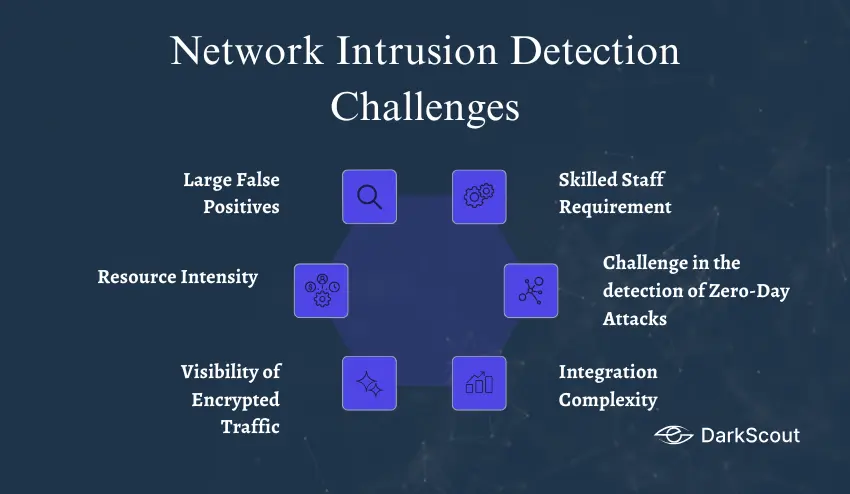
1. Large False Positives
False alarms generated by IDS solutions can be very numerous which is one of the most significant problems of this solution. When the normal network traffic is identified as suspicious, it may overload the security teams and lead to alert fatigue. This complicates the process of detecting actual dangers in a short time.
2. Resource Intensity
Detection of intrusion involves deep packet inspection and continuous monitoring which may consume many resources. Organizations that have high traffic can have large hardware and trained personnel to manage the traffic.
3. Visibility of Encrypted Traffic
As the application of encryption grows, the IDS tools might find it difficult to examine traffic in detail. Although encryption enhances security, it also conceals potentially malicious activity to the detection systems.
4. Skilled Staff Requirement
Intrusion detection tools are not plug and play. They need to have trained personnel to install, tune and control. In the absence of knowledge, organizations may fail to interpret alerts properly or have gaps in detection.
5. Challenge in the detection of Zero-Day Attacks
Signature systems are effective with known threats, but they tend to fail with a zero-day exploit or new attack technique. Although the anomaly detection can be useful, it is not foolproof and may add false positives.
6. Integration Complexity
IDS tools are effective when combined with firewalls, SIEMs and other platforms. These integrations however may be complicated to install and maintain to organizations that may have limited resources.
Conclusion
Having a powerful network intrusion detection system (NIDS) is no longer a luxury, but an absolute requirement of every organization that cares about security. As cyber threats are increasingly complex and commonplace, intrusion detection offers the awareness and notifications required to prevent attacks prior to their harm.
With tools such as DarkScout, Snort, Suricata, and Zeek, as well as enterprise solutions such as Palo Alto and Cisco Firepower, there is a plethora of options to find the solution that fits the needs and budget. The correct decision will be based on the size of your network, the security needs, and expertise at hand.
Nonetheless, the implementation of an IDS is not the whole solution. Adhering to best practices, comprehending the complications, and planning the future of intrusion detection are sure to make these tools have real value. Making your defense more resilient and strong by combining intrusion detection with other security layers, constant staff training, and updates.



