You think you are safe because you have secured the primary domain of your site? Think again. Most cyberattacks are not front-door. Rather, the attackers seek to find neglected subdomains that provide access to forgotten applications, testing environments, or ancient logins. Such weak points can be overlooked but are useful to hackers.
Here is the issue though: the vast majority of companies are not even aware of the number of subdomains they possess. Developers keep staging apps online, teams spin up test sites, and cloud services generate obscure URLs. All this increases your attack surface and no one notices. It is the equivalent of locking your house and leaving the back gate open.
This is where a subdomain finder comes in. Using the right tools, you can discover all the hidden subdomains affiliated to your domain, scan them to identify potential risks, and secure them before they are exploited by attackers. This guide will teach you what subdomains are, how enumeration is performed, what kinds of subdomain finders exist, and which ones I have the most trust in 2025.
What is a Subdomain?
A subdomain is something that is added to your main domain name. As an example, in blog.example.com, the subdomain is blog. Subdomains are used by companies in blogs, applications, testing, and region-specific websites.
The distinction between a domain and a subdomain is easy. A domain is a primary site and subdomains refer to distinct areas or services. They tend to be handled in different ways and thus can be exposed to danger when forgotten.
The importance of knowing about subdomains is that hackers adore attacking them. Most of the breaches occur because a business has left a test site or an old application running on a sub domain. This is why you should have a trustworthy subdomain finder to trace all of them.
You May Also Like: 7 Best Website Scanner Tools for 2026 (Compared & Reviewed)
What is Subdomain Finder?
A subdomain finder is an application that assists you to find all the subdomains of a domain. These tools operate in various ways. There are those that do DNS lookups, others apply APIs or brute-force methods, and others use public records.
The primary justification of using a subdomain finder is security. Mapping all your subdomains gives you a visibility to assets that would otherwise be forgotten. This visibility is important to security professionals, bug bounty hunters and IT teams.
A subdomain finder can be included in your attack surface management process when used properly. It is the initial step to sealing security loopholes.
What is Subdomain Enumeration?
Subdomain enumeration is a process of systematically determining all active and dormant subdomains associated with a domain. It is more than mere scanning because it involves a combination of several discovery methods.
The two major methods are passive enumeration and active enumeration. Passive approaches rely on the use of publicly accessible data such as search engines, APIs, and SSL certificates. Brute-forcing using wordlists or direct queries to DNS servers are active.
Subdomain enumeration is used by ethical hackers and penetration testers to identify weak points. When an organization does not go through this procedure, hackers may discover secret access points earlier than the company. It is because of this that it is critical to pair enumeration with a powerful subdomain finder.
Types of Subdomains Finders
Not all subdomain finders work the same way. I have observed that, over the years that tools may be fast, deep, or accurate. There are five general types, and each has its pros and cons.
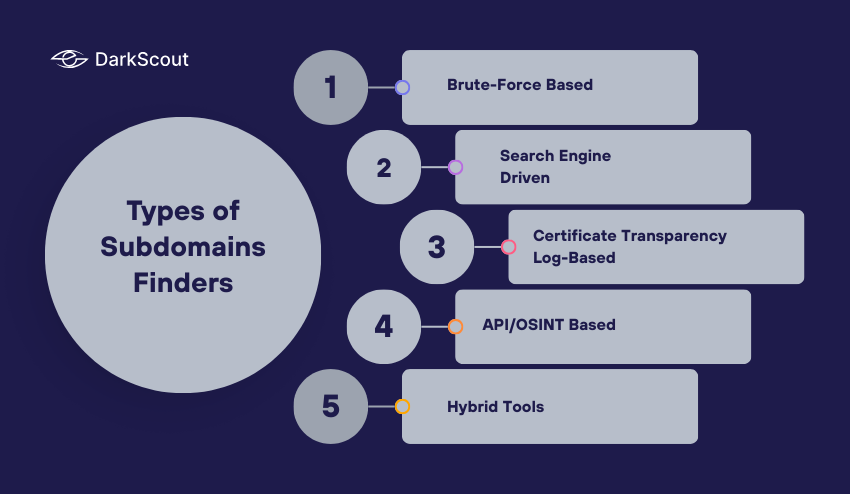
1. Brute-Force Based
These programs have a large database of common subdomain names and add it to your domain. As an example, they can make attempts with such words as mail, login, or test to determine whether subdomains of this kind are available. Brute-force methods are simple to code and effective when you are trying to find predictable naming patterns. The downside is velocity. It can be time consuming and consume a lot of resources when your wordlist is so big. However, brute-force subdomain finders are feasible in the case of smaller targets or speedy checks.
2. Search Engine Driven
Google and Bing are two of the most popular search engines that crawl and index millions of web pages including subdomains. These are retrieved by special queries (dorks) in search engine based finders. The advantage of this is efficiency. You can quickly access subdomains that are already visible on the Internet. This will not discover unindexed or private subdomains, so it should be used as part of a wider discovery strategy.
3. Certificate Transparency Log-Based
Each time a website issues an SSL/TLS certificate, a record is made in certificate transparency logs. These logs are accessible and can be searched to discover new or obscure subdomains. A subdomain may not be visible in search engines, but with a certificate, it will be visible here. This renders CT log-based finders useful in the detection of newly generated or internal resources. A lot of security teams will look through these logs on a regular basis to keep ahead of the attackers who are doing the same.
4. API/OSINT Based
SINT (Open-Source Intelligence) is the gathering of information that is publicly available. Subdomain finders that operate on an API basis look up this information on services like SecurityTrails, Shodan, or VirusTotal as a quick way of getting the information. The greatest advantage is convenience. Rather than putting heavy scans on your own, you can query these databases and get the results in a few seconds. API based finders are great when you need a quick audit or a precise data without the overheads of brute forcing.
5. Hybrid Tools
Some of the most effective contemporary tools integrate several approaches in a single one. To give an example, Amass combines passive data retrieved through APIs, active brute-forcing, and certificate transparency logs. Hybrid tools provide a more comprehensive view of your attack surface. They are more resource-consuming but provide more in-depth findings, and this is why penetration testers and bug bounty hunters usually use them.
The selection of the correct type of subdomain finder depends on your objective. In case you want to get a quick overview, search engine or API tools might suffice. Hybrid tools are the more intelligent option when you require the details of a penetration test or bug bounty program. The best results are typically obtained by combining several methods.
You May Also Like: Network Security Scan: 5 Critical Tips to Protect Your System
The Significance of Finding Subdomains in Cybersecurity
The neglect of subdomains is similar to locking the front door and leaving the windows open. Hackers are aware of this, this is why they do take an active role in seeking out forgotten subdomains. These entry points are usually less secure than the main domain since they are not always given the same monitoring or updates.
- Subdomains when unmonitored, can create severe vulnerabilities. Examples of such are as follows:
- Obsolete software that is run by old applications and can be exploited by the hackers.
- Abandoned databases which could still have sensitive customer or business information.
- Cloud services that are improperly configured and leak files or credentials.
- Internal dashboards, which are not intended to be public, but which become accessible online.
I have observed how most businesses underrate this risk. Staging sites or temporary services that have continued to be active years after the audits are common to find. In one instance, a single exposed subdomain gave attackers the opportunity to circumvent security measures and access sensitive records.
That is why the subdomain finder is so important. It assists you to view what the hackers may view and seal the loopholes before they can be a problem. When you incorporate subdomain discovery as a part of your security practice, you minimize blind areas and reinforce your security.
Top 7 Subdomain Finder Tools for 2025
The trick to finding a proper subdomain finder is not to find the best tool, but the tool that fits your workflow. There are those that are fast, those that are deep and those that integrate well with other security systems. The following are the best tools that have been outstanding in 2025, in terms of efficiency, reliability, and field use.
1. DarkScout
- What it is: DarkScout lightning-fast subdomain scanner written in Rust.
- Pros: Very light, efficient, and performance optimized, which makes it ideal to use by bug bounty hunters who require fast results.
- Weaknesses: The ecosystem is small compared to more established tools such as Amass. Not the most suitable one when it comes to large-scale, detailed mapping.
- Best used: Fast, targeted reconnaissance in bug bounty or red team engagements.
2. Sublift3r
- What it does: One of the most popular subdomain finders of the open-source category.
- Advantages: Simple to operate, very quick, and uses multiple search engines (Google, Bing, Yahoo, Netcraft, VirusTotal).
- Disadvantages: This may not detect deeper or more obscure domains, it can generate overlapping or duplicate results which may require filtering.
- Best applied: Immediate searches where the results must be provided in minutes and not hours.
3. Amass
- What it does: A powerhouse in the subdomain enumeration category, with passive/active techniques, graphing and visualization.
- Pros: Comprehensive to the extreme; can be combined with APIs, OSINT and DNS resolvers. Used in commercial pentesting reports.
- Disadvantages: Less fast than lightweight tools, and also with a higher learning curve.
- Best used in: Large-scale reconnaissance work where precision and detail is more important than speed.
4. Nmap
- What it does: A standard network scanner which can extend its own scripts.
- Pros: Versatility; able to shape subdomain discovery, with port scans, banner grabbing and vulnerability scanning. Perhaps one of the most reliable security tools in the world.
- Cons: In terms of enumerating subdomains in a bubble it is slow; unless you create optimized custom scripts. It just requires more work than the typical, specialized tools.
- Who it is best suited to: Security professionals who would like to use one tool to scan subdomains, ports, and services.
5. SubFinder
- What it does: It is a fast, passive subdomain scanner.
- Advantages: It is not heavy, it is noiseless, and has minimal false positives. Can be scripted to CI/CD pipelines or bug bounty pipelines
- Weaknesses: It is a passive tool, and will not brute-force or dig deeper as Amass does.
- Best use: Reconnaissance missions where you need noiseless, dependable results without alerting the targets.
6. SecurityTrails (API)
- What it is: a business offering that includes one of the most comprehensive DNS and subdomains data sets you can ask for.
- Advantages: API-based, best to be automated, scripted and built into pipelines. Great for enterprise monitoring.
- Disadvantages: it’s not free, it has different pricing tiers depending on queries, it offers limited manual use of the tool, and is not linked to the API.
7. Assetfinder
- What it does: A very fast subdomain discovery tool built in Go.
- Advantages: Assetfinder is able to fetch results from lots of sources very quickly. Perfect for bug bounty hunters looking for a quick win.
- Drawbacks: Doesn’t go as deep or advanced as Amass and can only surface-level discovery well.
- Best for: Systems where speed and simplicity are given more priority over depth.
Risks of Ignoring Subdomain Discovery
Subdomains are a serious security oversight. Attackers actively target their greater vulnerability in comparison to the primary domain.
- Data leaks: Leakage of sensitive data can be caused by forgotten apps or staging environments.
- Phishing vulnerability: Hackers have the ability to spoof subdomains in order to trick users or steal credentials.
- Compliance issues: The presence of hidden subdomains can lead to regulatory non-compliance with GDPR, HIPAA, or PCI DSS.
- Subdomain takeovers: Orphaned subdomains, those that are used to reach services that have not been claimed, can be hijacked.
- Loss of reputation: A compromised subdomain will have an impact on the customer trust and brand image.
I have seen companies suffer breaches because they had not noticed the discovery of subdomains. Subdomain finder is not a luxury but a must because it is the only means of finding and securing such hidden assets before the attackers.
Conclusion
The subdomains are usually overlooked, and they may be the Achilles heel of your security. A quality subdomain finder provides you with the visibility, control, and protection of these hidden assets.
By getting to know the meaning of subdomain, the process of enumerating and the various types of finders, you can make more intelligent moves to secure your business.
Begin with one or two of the tools in the list above. After you get used to them, incorporate them into your normal security practice. The earlier you are able to detect risks, the quicker you are able to avoid them.
Your area of expertise is as weak as the weakest part of the area. Find a subdomain finder now and prevent attackers exploiting the hole before they discover it.